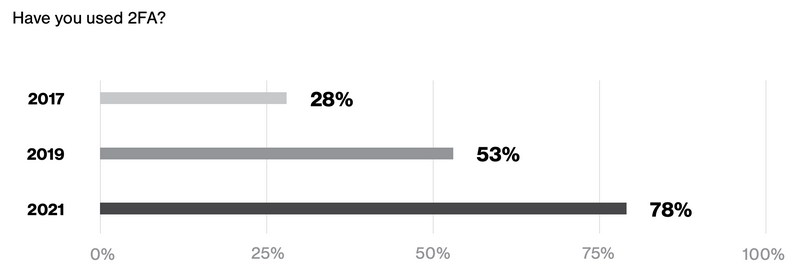
Most of you folks are already aware of password authentication and MFA (Multi Factor Authentication). Just a little bit of history: the first password was used in the Compatible Time-Sharing System at MIT in 1961. The MFA, however, was introduced later in 1986 with the first RSA Tokens, and recently MFA has become widely used among consumers. According to MFA digital authenticator company Duo’s annual State of the Auth Report, two-factor authentication has become notably more prevalent over the last two years, with 79% of respondents reporting having used it in 2021, compared to 53% in 2019 and 28% in 2017.
As you will see, there are many multi factor authentication methods, but they are not built the same.
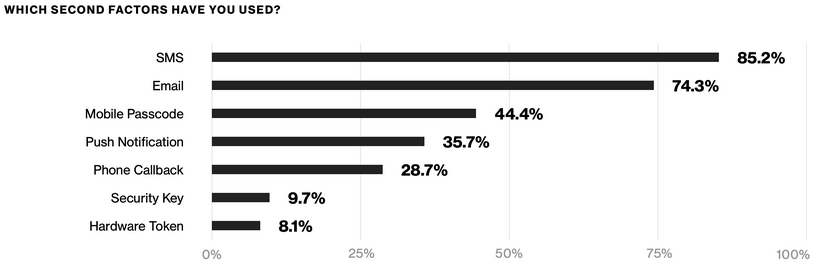
While SMS is certainly more secure than no MFA, a security key is much better. In this blog series you will have the chance to deep dive into the magical world of encryption, pgp keys, security keys and hardware tokens and why they are considered more secure than other multi-factor authentication methods.
Many companies have helped to make MFA more user-friendly, one of them is Yubico. In this article we will cover the basics using Yubico’s security key called Yubikey.
What’s a Yubikey?
Yubikey is a small piece of hardware device typically comes in USB-A or USB-C type connectors. These devices are capable of generating a variety of security functions like one-time passwords, secure static passwords, smart-card capability and supports OpenPGP. You can compare various types of Yubikeys here.
Getting started
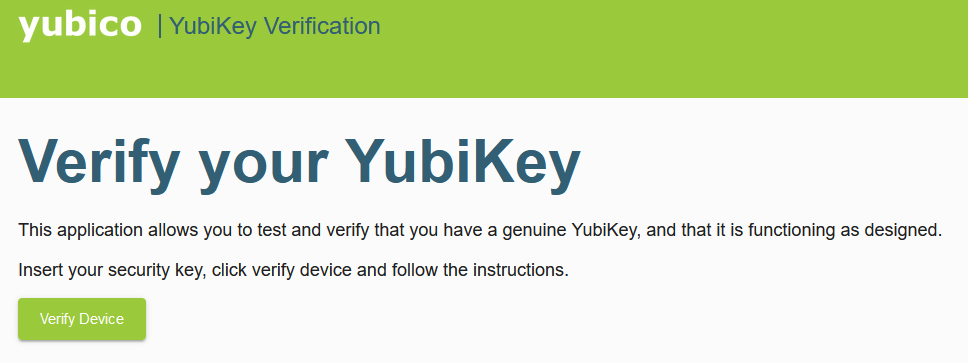
Once you have your Yubikey, you can verify if it is genuine. Go to https://www.yubico.com/genuine/ and follow the verification process. Once complete, the website will notify you if the device is authentic.
This website helps prevent supply chain attacks by verifying YubiKey device attestation certificates that have been signed by specific Yubico certificate authorities.
My suggestion is to have at least two Yubikeys and configure them both and store the second key in a secure and safe place.
The next step is to install the Yubikey manager based on your OS. Once you download you can setup three PINs - one for its FIDO2 function, one for PIV (smart card), and one for OpenPGP.
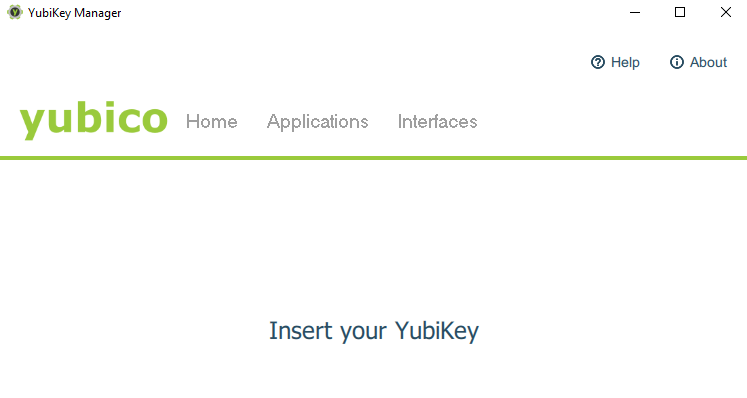
Keep in mind that if you enter the FIDO2 PIN incorrectly 3 consecutive times, you will need to reinsert the key before attempting to enter the PIN again. If you enter the PIN incorrectly a total of 8 times, the FIDO2 function will be blocked and will need to be reset, which will also unregister the key from any accounts it has been linked to for FIDO U2F or FIDO2.
To setup your Yubikey, you can visit https://www.yubico.com/start and select your Yubikey and follow the instructions for each service where you want to configure MFA. The process is pretty straight forward. You will have access to a Youtube tutorial and have an official guide for each service.
Congratulations. Now you have secured your applications.
If you want a list of applications and services that support Yubikey, you can visit here.